导言
The CUDA Execution Model: how the CUDA architecture handles the execution of code in parallel.
这篇将聚焦于CUDA的基础知识,基本概念,
linux下通过按照如下修改.ssh/config设置账号密码,并 ssh -vT [email protected],成功后输出Hi Kirrito-k423! You've successfully authenticated, but GitHub does not provide shell access.。
1 | # .ssh/config |
There are tons of identical solutions over the internet for defining proxy tunnel for git’s downloads like this one, which all is by setting git’s https.proxy & http.proxy config. but those answers are not working when you try to clone/push/pull etc. over the ssh protocol!
For example, by setting git config --global https.proxy socks5://127.0.0.1:9999 when you try to clone git clone [email protected]:user/repo.git it does not go through the defined sock5 tunnel!
1 | # Method 1. git http + proxy http |
%h %p 是host和post的意思
或者
After some visiting so many pages, I finally find the solution to my question:
1 | [step 1] create a ssh-proxy |
To install connect on Ubuntu:
1 | sudo apt install connect-proxy |
1 | ssh -vT -o "ProxyCommand connect -S 127.0.0.1:7890 %h %p" [email protected] |
post request forward is an all-in-one solution.
1 | interface: warp |
latest handshake: 89 days ago demonstrate wg is done for a long time. At the same time mtr github.com shows no output prove the bad situation.
STEP1: first try is to bring the wg-proxy up again
1 | python register.py #自动生成warp-op.conf,warp.conf和warp-helper |
and test brainiac machine is back online
Sometimes,it‘s the big log fault.
1 | # find file |
1 | t00906153@A2305023964 MINGW64 ~/github |
Z:\shaojiemike\Documents\文献\计算机网络目录下。这里先使用fjw的脚本。register.py,获得私钥和分配的ip1 | [Interface] |
main.sh修改包的3个字节。apt-get install nftables/etc/default/warp-helper文件填写对应的wg-conf里Endpoint。比如: ROUTING_ID=11,45,14
UPSTREAM=[2606:4700:d0::a29f:c001]:500
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
2. 最后开启路由表,Root权限运行` ip route add default dev warp proto static scope link table default`
## WARP on OpenWRT
* 目的:为了防止大量流量通过WARP,导致被官方封禁,所以只在OpenWRT上配置WARP分流github的流量。
* 实现思路:
* 运行python脚本,通过github的API获得所有的github域名ip,
* 使用iptables的warp_out表,将目的地址为github域名ip路由到WARP的虚拟网卡上。
### WARP Wireguard Establishment
```bash
python register.py #自动生成warp-op.conf,warp.conf和warp-helper
mv warp-helper /etc/default
# cat main.sh
# cat warp-op.conf
vim /etc/config/network #填写warp-op.conf内容,默认只转发172.16.0.0/24来测试连接
ifup warp #启动warp, 代替wg-quick up warp.conf
bash main.sh #启动防火墙实现报文头关键三字节修改
nft list ruleset #查看防火墙,是否配置成功
wg #查看warp状态,测试是否连接成果
这时还没创建warp_out路由表,所以还不能通过WARP出数据。
1 | #/etc/config/network |
然后WebUI点击apply 或者命令行运行ifconfig warp down && ifup
添加了WARP的网络出口后,路由器不在只是通过WAN出数据。防火墙需要更新: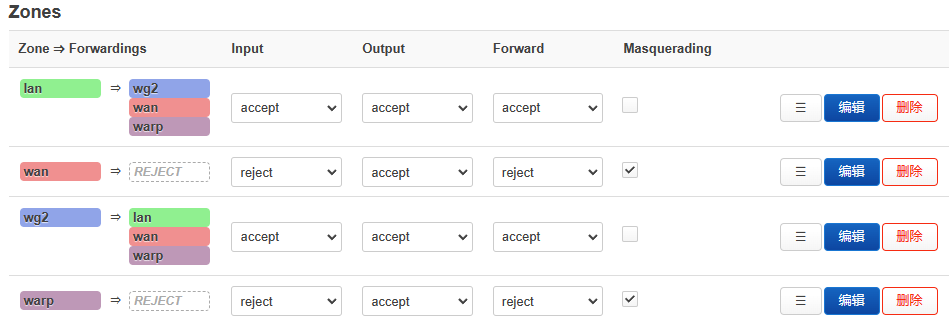
wget --bind-address=WARP_ip来模拟10: from all lookup main suppress_prefixlength 11000: from all lookup warp_out,优先级10001 | root@tsjOp:~/warp# ip rule |
1 | cd ip_route |
对所有github域名的ip执行类似ip ro add 192.30.252.0/22 dev warp proto static table warp_out操作。
1 | mtr www.github.com |
修改/etc/rc.local
1 | # Put your custom commands here that should be executed once |
基于1.1.1.1 的安装windows版本直接白嫖
暂无
暂无
https://gist.github.com/iBug/3107fd4d5af6a4ea7bcea4a8090dcc7e
glados