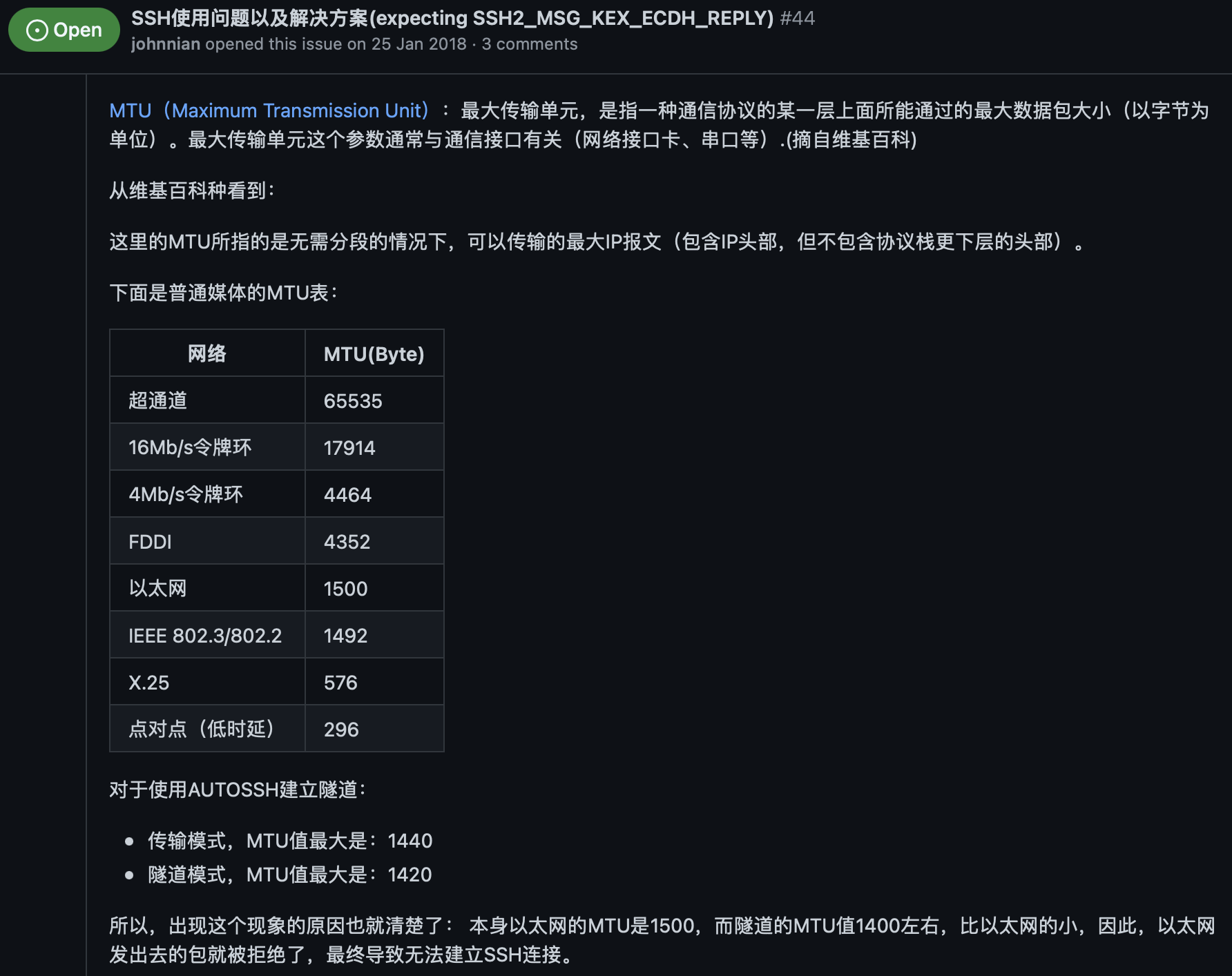
Wireguard Server 2 Server in OpenWRT
Proxy in terminal
ssh config
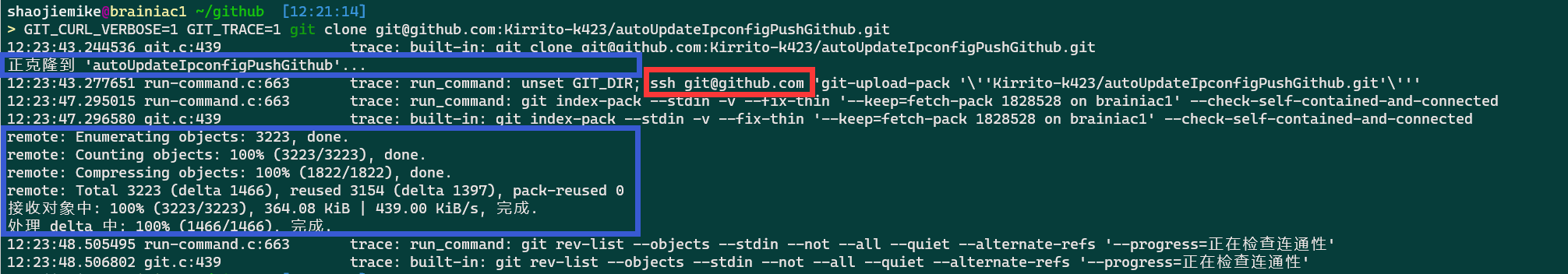
linux下通过按照如下修改.ssh/config设置账号密码,并 ssh -vT [email protected],成功后输出Hi Kirrito-k423! You've successfully authenticated, but GitHub does not provide shell access.。
1 | # .ssh/config |
debug ssh clone/push
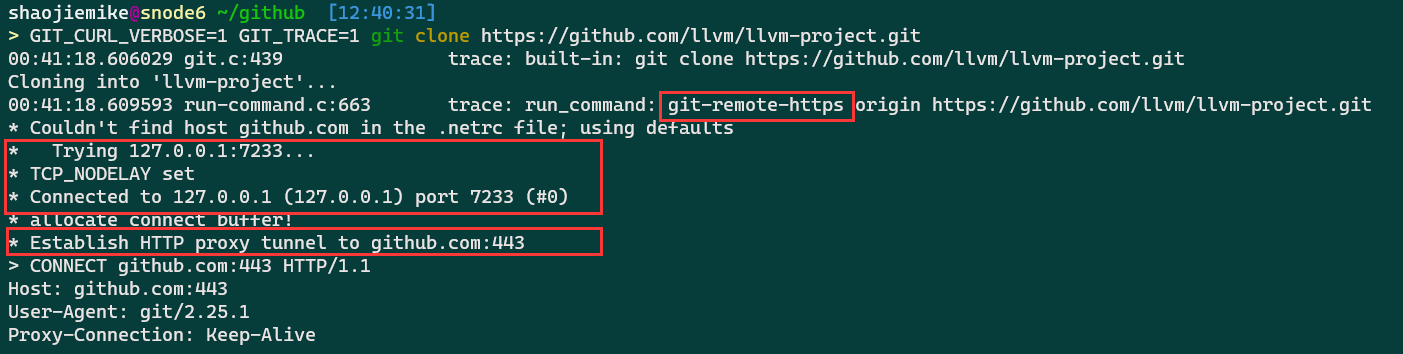
http代理
There are tons of identical solutions over the internet for defining proxy tunnel for git’s downloads like this one, which all is by setting git’s https.proxy & http.proxy config. but those answers are not working when you try to clone/push/pull etc. over the ssh protocol!
For example, by setting git config --global https.proxy socks5://127.0.0.1:9999 when you try to clone git clone [email protected]:user/repo.git it does not go through the defined sock5 tunnel!
1 | # Method 1. git http + proxy http |
%h %p 是host和post的意思
或者
After some visiting so many pages, I finally find the solution to my question:
1 | [step 1] create a ssh-proxy |
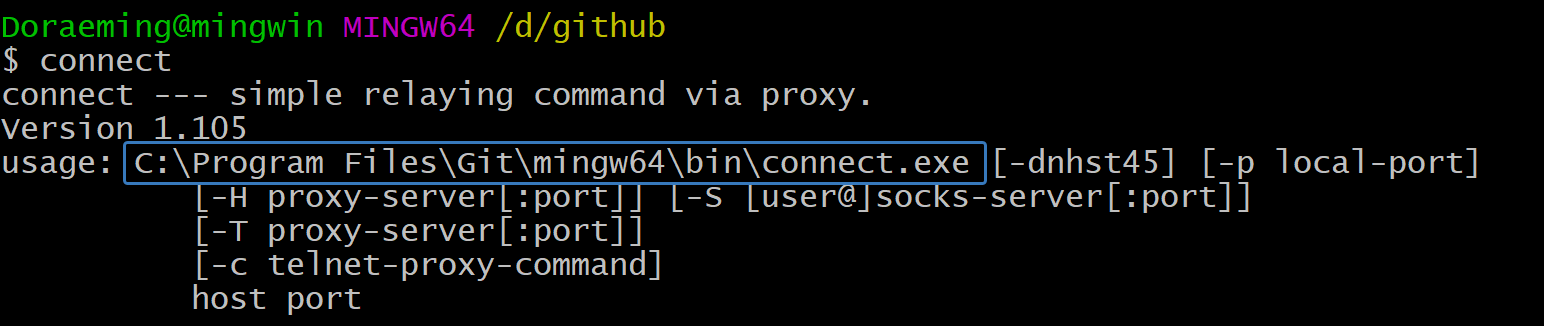
To install connect on Ubuntu:
1 | sudo apt install connect-proxy |
ssh代理
1 | ssh -vT -o "ProxyCommand connect -S 127.0.0.1:7890 %h %p" [email protected] |
Wireguard 代理
post request forward is an all-in-one solution.
1 | interface: warp |
latest handshake: 89 days ago demonstrate wg is done for a long time. At the same time mtr github.com shows no output prove the bad situation.
STEP1: first try is to bring the wg-proxy up again
1 | python register.py #自动生成warp-op.conf,warp.conf和warp-helper |
and test brainiac machine is back online
常见情形
大文件提交
Sometimes,it‘s the big log fault.
1 | # find file |
请求被拦截
1 | t00906153@A2305023964 MINGW64 ~/github |
常见问题
参考文献
简介
- WireGuard 是由 Jason Donenfeld 等人用 C 语言编写的一个开源 VPN 协议,被视为下一代 VPN 协议,旨在解决许多困扰 IPSec/IKEv2、OpenVPN 或 L2TP 等其他 VPN 协议的问题。它与 Tinc 和 MeshBird 等现代 VPN 产品有一些相似之处,即加密技术先进、配置简单。
- 从 2020 年 1 月开始,它已经并入了 Linux 内核的 5.6 版本,这意味着大多数 Linux 发行版的用户将拥有一个开箱即用的 WireGuard。
- WireGuard 作为一个更先进、更现代的 VPN 协议,比起传统的 IPSec、OpenVPN 等实现,效率更高,配置更简单,并且已经合并入 Linux 内核,使用起来更加方便。
常见VPN方法比较
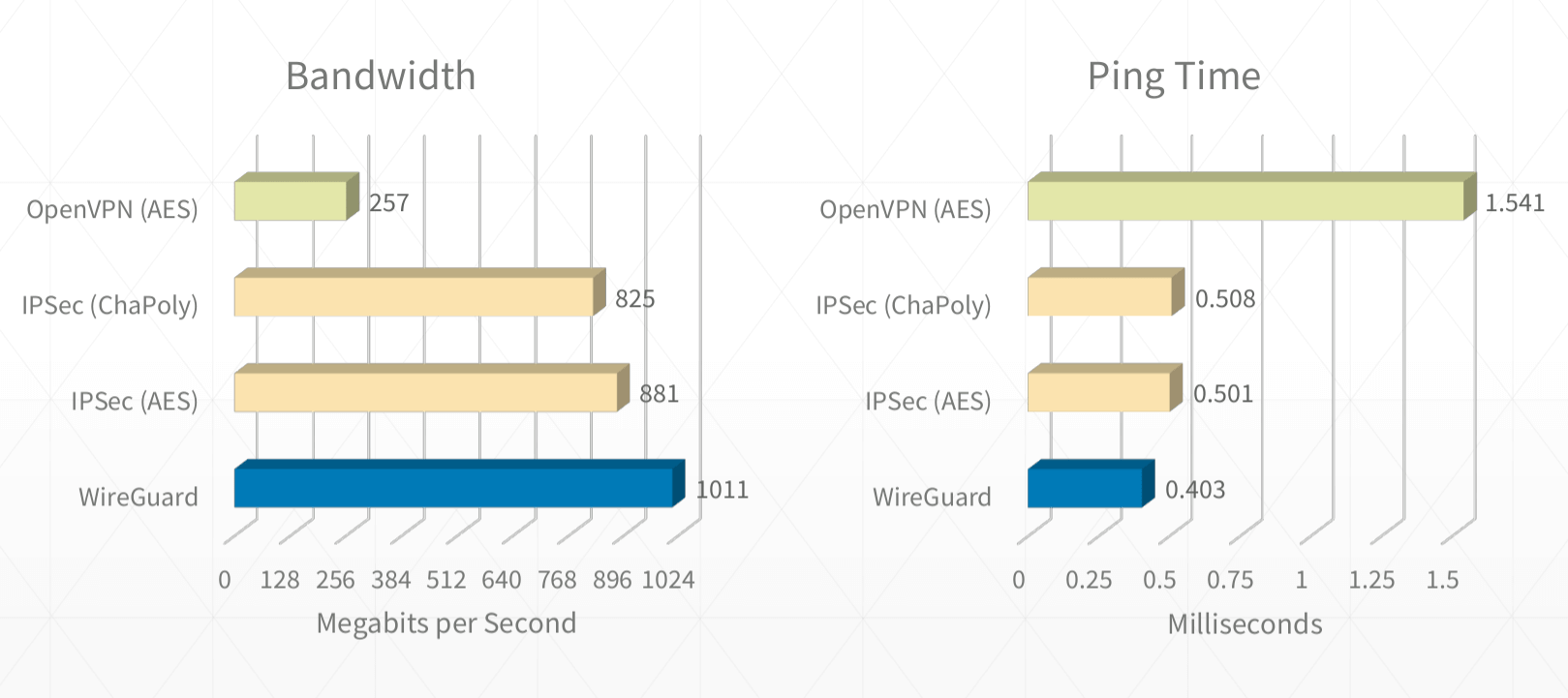
- wireguard 精簡、速度極快:
- 只有 4000 行程式碼,是最精簡的 VPN 協議。对比下 OpenVPN,大约有 10 万行代码。
- WireGuard 利用内核空间处理来提升性能(更高吞吐和更低延迟),同时避免了不必要的内核和用户空间频繁上下文切换开销。
Wireguard客户端连接Debug
- 首先,服务端的ip或者域名能ping通
- 其次端口确定开放
> nc -z -v -u 4.shaojiemike.top 51822,wg是udp - 修改wg客户端配置文件,限制ip为wg设置的内网段,
AllowedIPs = 192.168.31.0/24,10.0.233.1/24.然后ping 192.168.31.1测试 - 如果还不行,判断为wg的VPN包被中间网关识别并丢弃
配置文件
配置详解参考中文文档
PersistentKeepalive
- 一端位于 NAT 后面,另一端直接通过公网暴露
- 这种情况下,最简单的方案是:通过公网暴露的一端作为服务端,另一端指定服务端的公网地址和端口,然后通过 persistent-keepalive 选项维持长连接,让 NAT 记得对应的映射关系。
[peer]里设定字段PersistentKeepalive = 25,表示每隔 25 秒发送一次 ping 来检查连接。
AllowedIPs
虽然AllowedIPs = 0.0.0.0/0与AllowedIPs = 0.0.0.0/1, 128.0.0.0/1包含的都是全部的ip。
但是前者在iptable里为default dev wg1,后者为两条0.0.0.0/1 dev wg1和128.0.0.0/1 dev wg1。
由于路由的ip匹配遵循最长前缀匹配规则,如果路由表里原本有一条efault dev eth0。使用前者会导致混乱。但是使用后者,由于两条的优先级会更高,会屏蔽掉原本的default规则。
前者的iptable修改如下:(macbook上)
1 | > ip route |
后者的iptable修改如下
1 | > ip route |
原理
建议看WireGuard 教程:WireGuard 的工作原理 和WireGuard 基础教程:wg-quick 路由策略解读,详细解释了wg是如何修改路由表规则的。
wireguard 运行原理以及配置文件
默认会产生51840的路由table,ip rule优先级较高。可以通过配置文件中添加PostUp来修改最后一个default的路由规则。
1 | root@snode6:/etc/wireguard# cat wg0.conf |
PostUp会产生下面的规则
1 | root@snode6:/staff/shaojiemike# ip ro show table default |
OpenVPN原理
OpenVPN原理通过在main添加all规则来实现
1 | # shaojiemike @ node5 in ~ [22:29:05] |
clash TUN模式
Macbook上的应用上的ClashX Pro的增强模式类似, 会添加如下配置,将基本所有流量代理(除开0.0.0.0/8)
1 | > ip route |
明显有代理死循环问题,如何解决???
1 | shaojiemike@shaojiemikedeMacBook-Air ~/github/hugoMinos (main*) [10:59:32] |
Wireguard 环境配置
wireguard-go: 安装客户端 wg-quick up config
wireguard-tools: 安装服务端 wg
Wireguard 常见命令
- 启动
wg-quick up wg1 - 关闭
wg-quick down wg1 - 查看状态
wg显示全部,或者wg show wg1显示wg1
wireguard开机启动
1 | systemctl enable wg-quick@wg1 --now |
使用wireguard 代理ipv6请求
- WireGuard 也支持 IPv6。OpenWRT 服务端,当然要allowed ip
fd00::aaaa:5/128、 - 注意:这是伪需求,为什么ipv6的流量需要走ipv6,不走wg,每个机器可以获得独立的公网ipv6,对于PT做种是很好的。
1 | brainiac1# cat wg-tsj.conf |
两次wireguard上网
修改sysctl.conf文件的net.ipv4.ip_forward参数。其值为0,说明禁止进行IP转发;如果是1,则说明IP转发功能已经打开。
需要执行指令sysctl -p 后新的配置才会生效。
两台机器的wireguard配置
注意中间需要NAT转换, 相当于把kunpeng机器的请求,隐藏成snode6的请求。在后一次wireguard转发时,就不会被过滤掉。
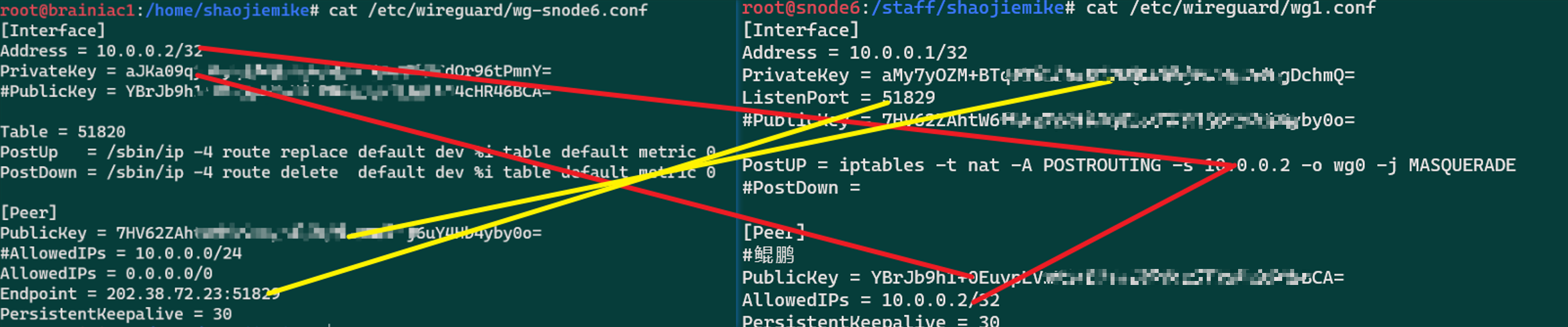
1 | PostUp = iptables -t nat -A POSTROUTING -s 10.1.0.0/24 ! -o %i -j MASQUERADE |
机器(Nas)使用Wireguard上网
问题场景
由于换了wg服务端,导致nas变成闭环的网络了。最后是通过群晖助手(Synology Assistant / Web Assistant)的设置静态ip才连接上机器,但是iptable被设置乱了。
静态连接上机器,首先在网页管理页面切换成DHCP(静态ip的DNS解析有误),iptable变成如下
1 | sh-4.4# ip ro |
注意iptable的修改是实时生效的。
思路
为了让nas上网我们需要满足两点
- 本地ssh eth0的222.195.90.2能访问机器(优先级更高)
- 其余网络走wg
1 | # 重要项如下 |
使用wg1配置如下:
1 | sh-4.4# cat /etc/wireguard/wg1.conf |
问题:服务端重启,Nas的wg客户端失联
要保留没有wg的时候访问服务端的eth0(114.214.233.xxx)的通路
1 | sh-4.4# ip ro s t main |
来自eth0的ssh与ping请求原路返回
源地址为自身IP的包走学校的路由器
目的:需要ssh和ping ipv4成功
修改netplan的配置文件
1 | # shaojiemike @ node5 in ~ [22:29:11] |
routing-policy会产生
1 | # shaojiemike @ node5 in ~ [22:30:33] |
由于2优先级高,使得ping和ssh的返回信包(源地址为自身机器IP的包)走table1 规则,而不是走
routes使得所有的table1都会走学校的路由器(202.38.73.254)
1 | $ ip route show table 1 |
衍生问题:网络请求的源地址不是自己吗?怎么确定的
开启wg后,网络请求源地址变成了10.0.33.2。不是202.38.73.217
1 | root@node5:/home/shaojiemike# ip ro |
但是外界ping的是202.38.73.217。返回包交换所以会产生源地址为202.38.73.217的包
wireguard 实现翻墙
- WireGuard 在国内网络环境下会遇到一个致命的问题:UDP 封锁/限速。虽然通过 WireGuard 可以在隧道内传输任何基于 IP 的协议(TCP、UDP、ICMP、SCTP、IPIP、GRE 等),但 WireGuard 隧道本身是通过 UDP 协议进行通信的,而国内运营商根本没有能力和精力根据 TCP 和 UDP 的不同去深度定制不同的 QoS 策略,几乎全部采取一刀切的手段:对 UDP 进行限速甚至封锁。
- 虽然对 UDP 不友好,但却无力深度检测 TCP 连接的真实性。
- 将 UDP 连接伪装成 TCP 连接不就蒙混过关了。目前支持将 UDP 流量伪装成 TCP 流量的主流工具是 udp2raw,但是有一款更强大的新工具: Phantun。
需要进一步的研究学习
暂无
遇到的问题
暂无
开题缘由、总结、反思、吐槽~~
参考文献
WireGuard 基础教程:使用 Phantun 将 WireGuard 的 UDP 流量伪装成 TCP
OpenWRT Installation on router
原理
原理在路由器的两个flash(firmware和firmware1)的两个系统里,写入一个支持图形化OpenWRT的新系统
查看路由器型号是否支持
查看系统型号[^1]:路由器默认是魔改的openwrt的系统:
1 | root@XiaoQiang:~# cat /etc/os-release |
刷入OpenWRT后:
1 | root@ax6s:~# cat /etc/os-release |
路由器开启dropbear
dropbear 是一种轻量级sshd服务
1 | nvram set ssh_en=1 # 不是1也退出1 |
修改/etc/dropbear/authorized_keys 来添加ssh公钥
Redmi-Ax6s实操
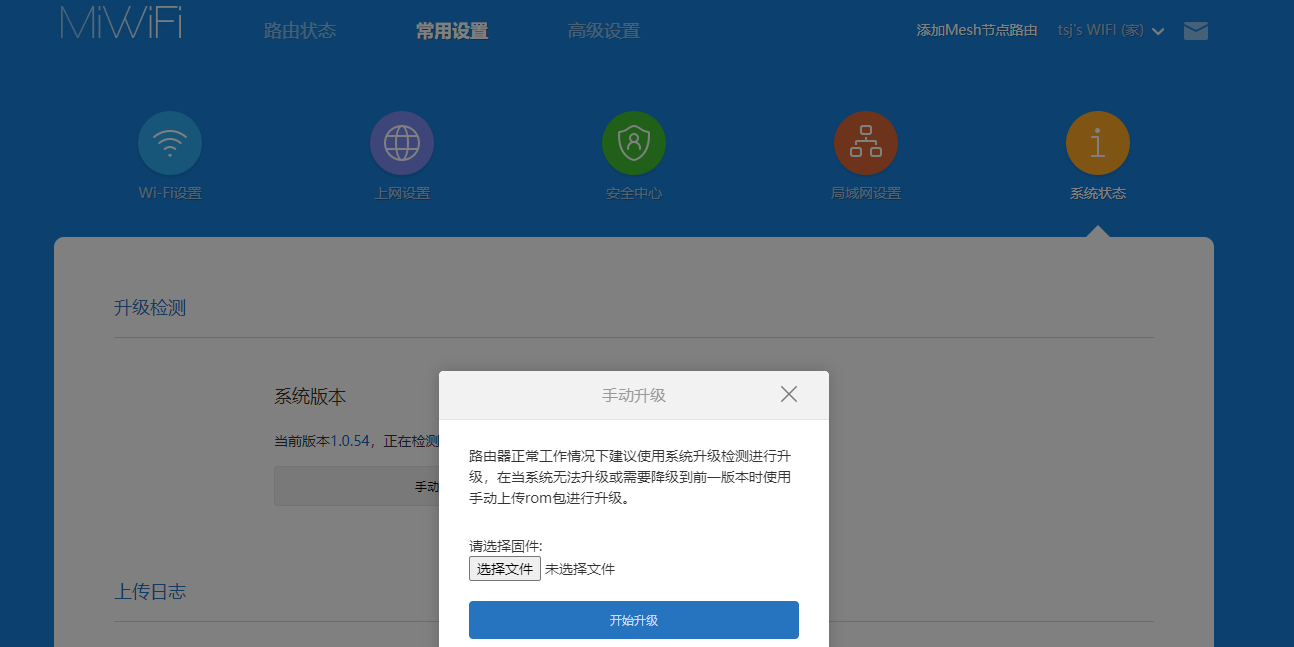
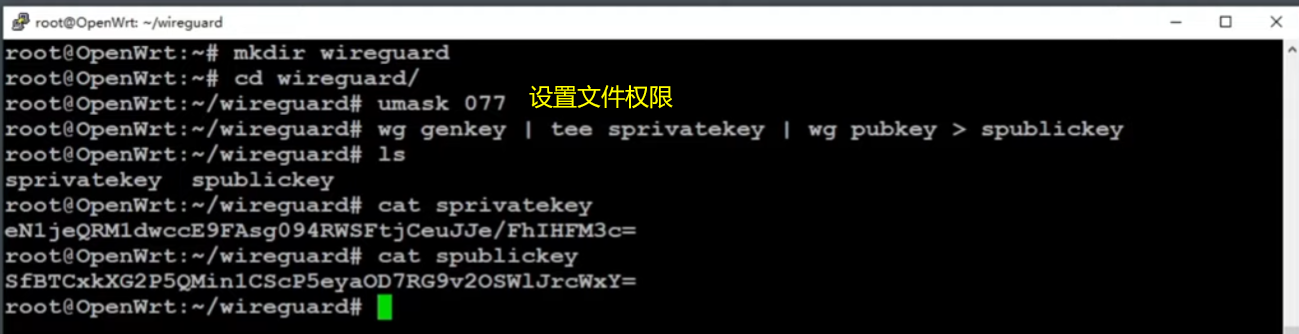
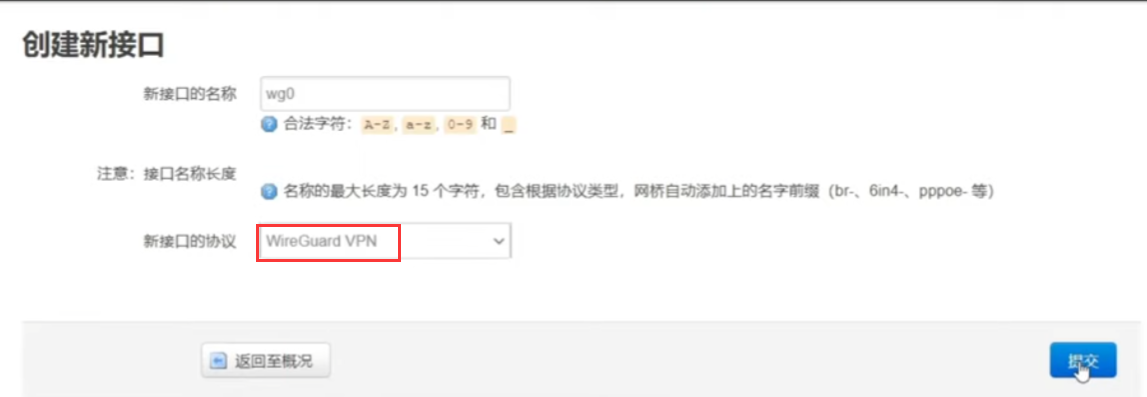
WireGuard Server in OpenWRT
OpenWRT换软件安装源
修改/etc/opkg/distfeeds.conf的配置,参考
下面为x86软路由的源(由于是snapshot的安装不了,内核不匹配),如果是arm的需要看对应架构代号。
1 | src/gz openwrt_core https://mirrors.ustc.edu.cn/openwrt/releases/22.03.3/targets/x86/64/packages |
比如ax6s
1 | [root@ax6s ~]$ cat /etc/opkg/distfeeds.conf |
可以通过cat /etc/os-release查看, 上面的如下
1 | root@OpenWrt:~# cat /etc/os-release |
WireGuard安装服务端程序
-
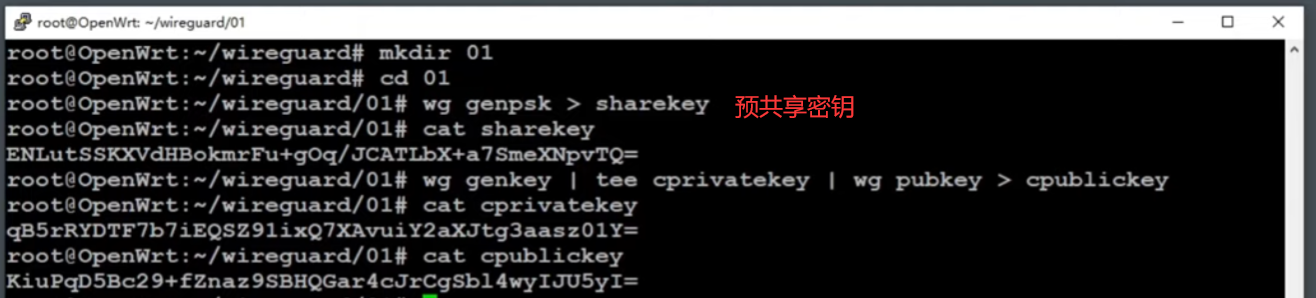
- 内置了wireguard(使用对等节点的公私钥加密)
OpenWrt安装WireGuard命令(eSir精品小包已集成WireGuard,无需安装)
1
2
3
4
5
6opkg update
opkg install luci-proto-wireguard luci-app-wireguard wireguard kmod-wireguard wireguard-tools
reboot
# x86
opkg install wireguard luci-app-wireguard luci-i18n-wireguard-zh-cn wireguard-tools
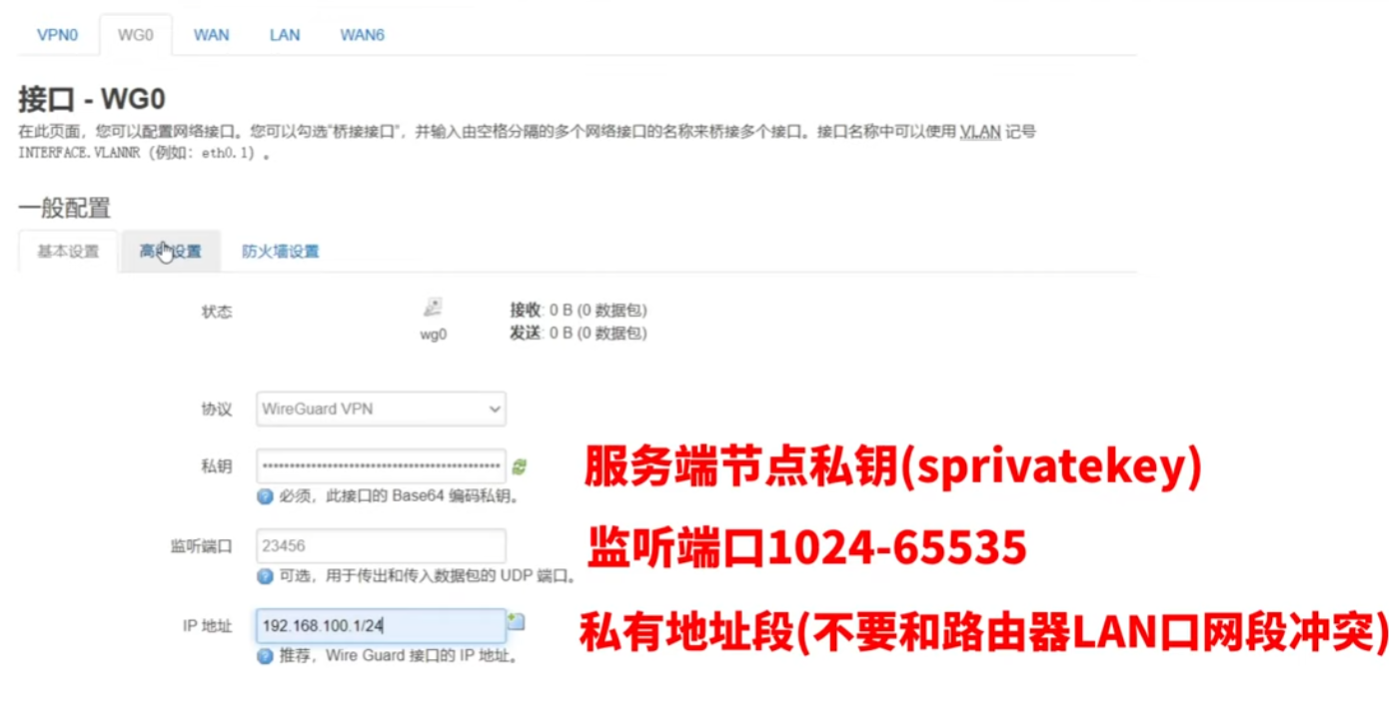
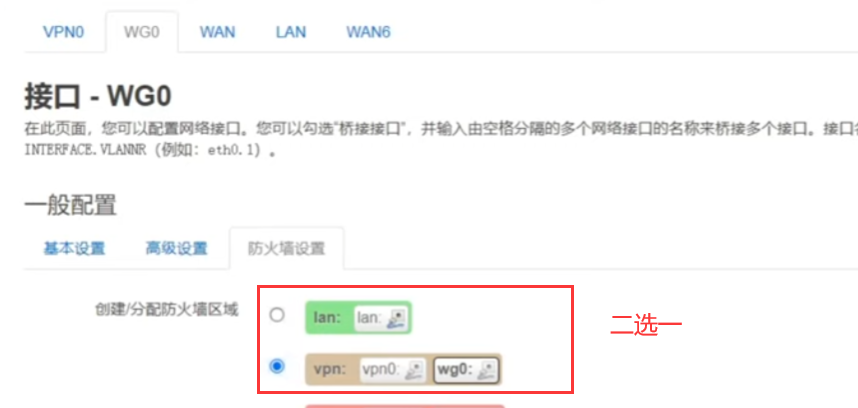
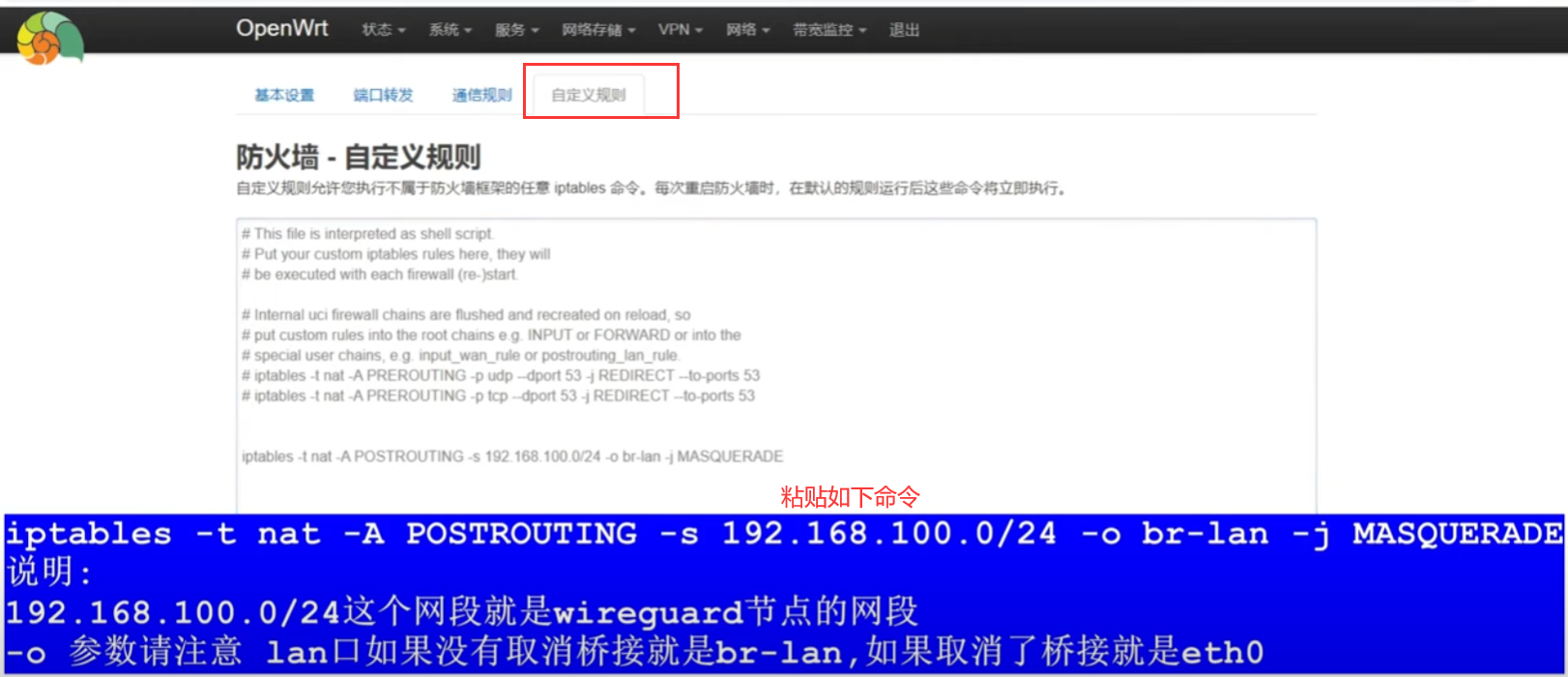
WireGuard服务端设置
WireGuard客户端设置
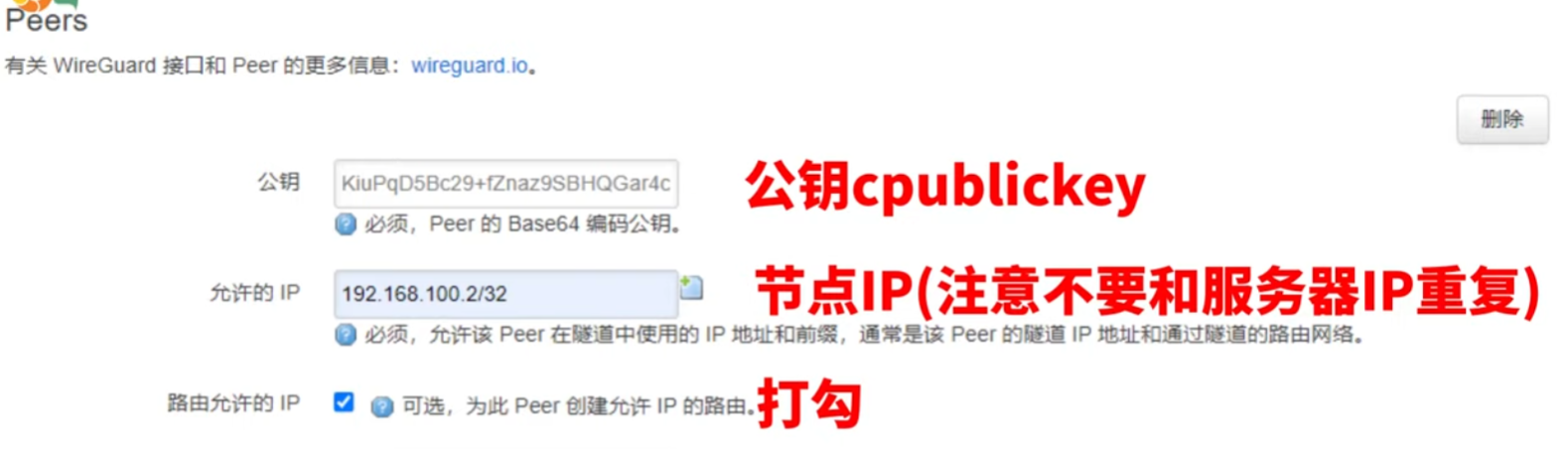
客户端模板文件test.conf
1 | [Interface] |
WireGuard配置匹配一览图
"[Interface] Address" is the address that gets assigned to the (virtual) network interface (e.g. wg0).
简单来说客户端和服务器端约定的相同的虚拟地址来通信。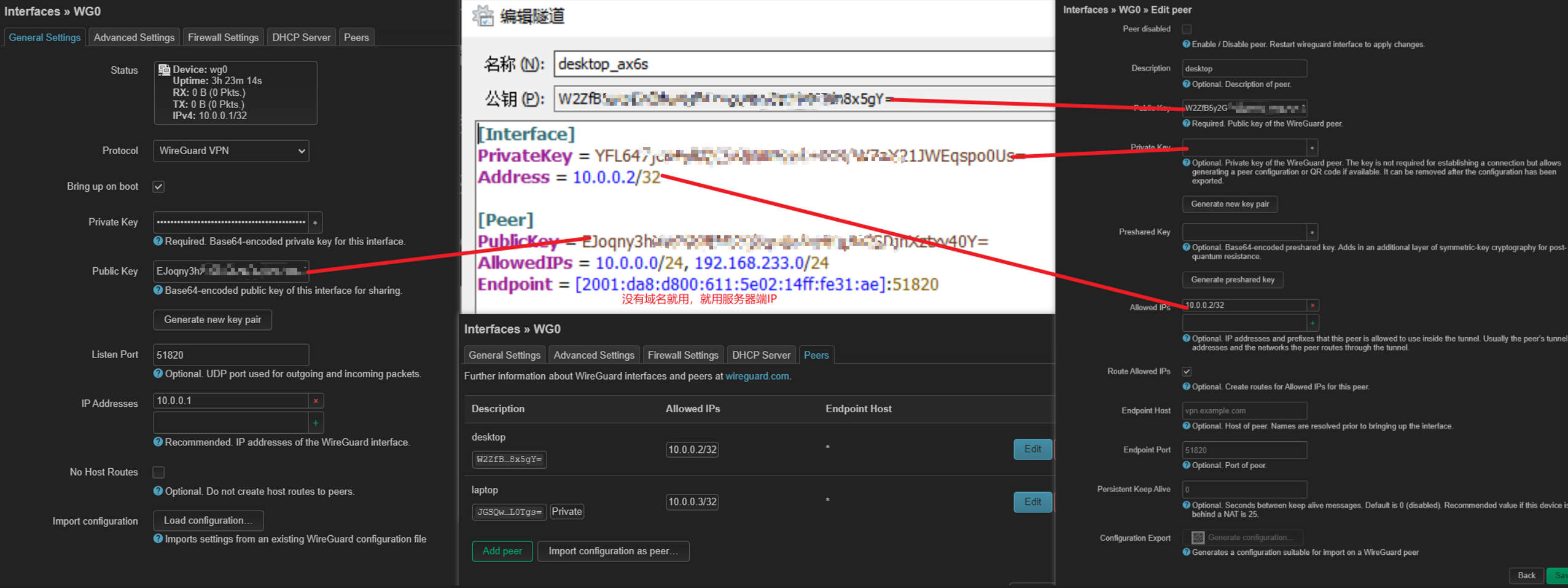
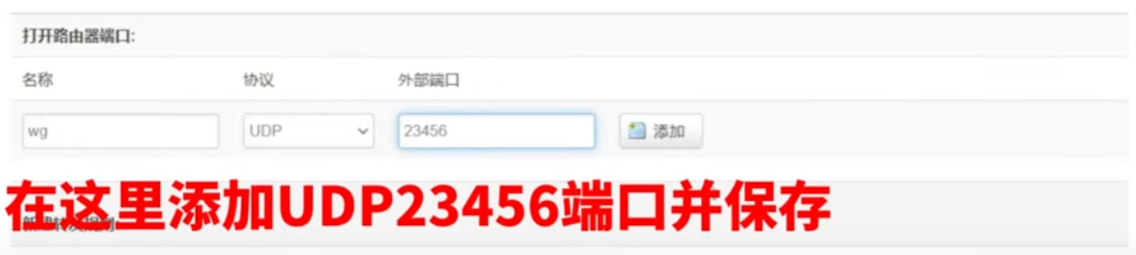
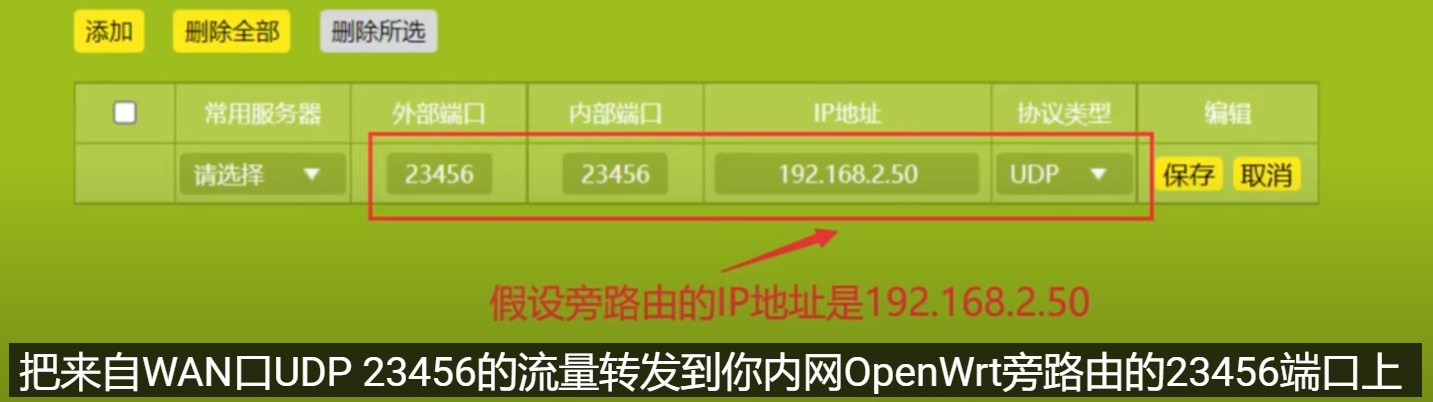
注意防火墙放行端口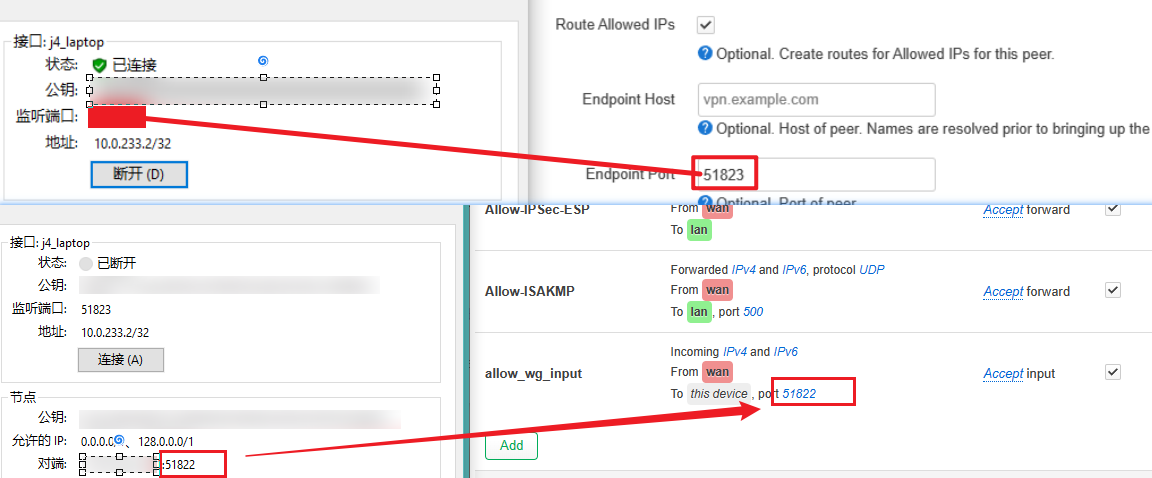
官方客户端软件下载
WireGuard常见问题
注意:如果连接不上
- 首先保证路由器有网,不是路由器下的电脑有网
- 上次师兄的电脑开了OpenVPN上网,导致路由器ipv6能ping通,但是不能上网
- 注意防火墙,一个是wan口允许某几个端口进来(wg连接请求)。另一个是wan能到wg,wg也能到wan,才能实现上网
- 至于和lan的关系,如果需要通过wg访问lan口下的设备(nas,电脑)再打开即可。
Clash in OpenWrt
- 安装版本来自github
- 但是由于DDNS会出问题,所以关闭了。(可以考虑2次wireguard蹭网和clash for linux)
- BT,PT有时也会被代理,需要注意。
安装编译好的 IPK 文件(openwrt 的软件包)
安装依赖
1 | #iptables |
重启后出现
注意不会代理ping,所以ping不通的话,可以用curl来测试代理是否生效。https失败可以尝试http
安装问题
1 | Collected errors: |
解决办法如下
1 | opkg update |
DDNS in OpenWRT
DDNS简介
Dynamic DNS: 根據網際網路的域名訂立規則,域名必須跟從固定的IP位址。但動態DNS系統為動態網域提供一個固定的名稱伺服器(Name server),透過即時更新,使外界使用者能夠連上動態使用者的網址。
cloudflare动态域名 或者阿里云动态域名的DDNS都是很好的选择。
定时脚本实现DDNS
1 | [root@ax6s ~]$ cat ddns.sh |
修改crontab -e
1 | PATH=/sbin:/bin:/usr/sbin:/usr/bin:/usr/local/sbin:/usr/local/bin |
OpenWRT 为局域网设备设置IPv6 DDNS
脚本围绕,打印邻居路由表命令
1 | [root@ax6s ~]$ ip -6 neigh | grep 2c:f0:5d |
新建 /usr/lib/ddns/dynamic_dns_iphelper.sh
1 |
|
新建 /usr/lib/ddns/getip_demo.sh
1 |
|
脚本chmod +x就行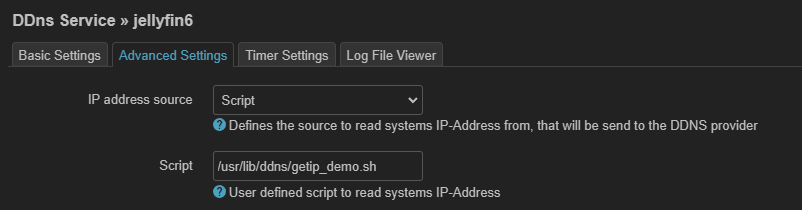
School Network
- 根据学校的网络通各个端口的说明,0号端口没有经过NAT,登录之后获得公网ipv4。但是IPv4封了许多端口(至少ssh的22端口是不行的)
- IPv6是直接可以ssh访问的。
参考文献
https://www.youtube.com/watch?v=F8z74oE71Gg&t=19s
https://xiumu.org/technology/openwrt-set-for-local-area-network-lan-equipment-ipv6-ddns.shtml